PlusPassword - Share passwords without revealing them
No revealing in plaintext, no copying to clipboard
tl;dr: PlusPassword is:
- A free tool (web app || Slack app & browser extension download page).
- That allows you to share passwords with others without revealing them in plaintext or copying to clipboard*.
…………………………………………………………………………………………………
🫵 Do you…
- Share passwords with others (coworkers / 3rd party vendors) more than once a week?
- And you know you shouldn’t be sharing them in plaintext over email / text / Slack...
- But you do so anyways because there isn’t a better alternative?
- Well, now there is!
💡 How does PlusPassword work?
-
Sharing password.
1. Set security options such as:
- Automatic logout after X hours.
- Restrict password paste to specific web domain.
- Email allowlist.
2. Generate access link.
3. Share link.
-
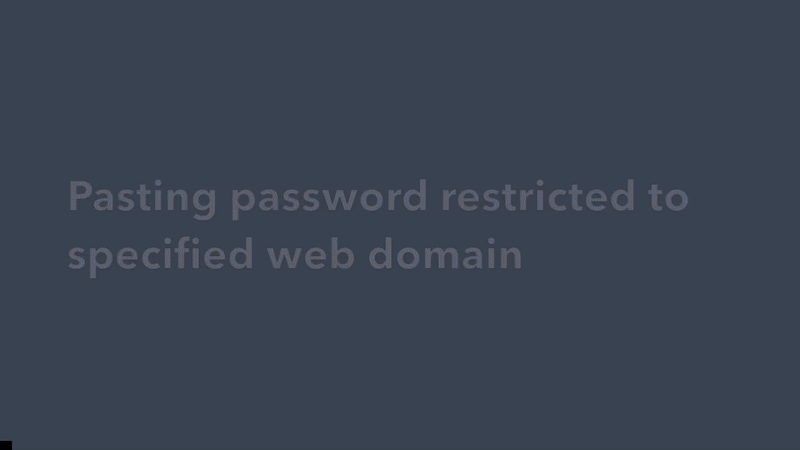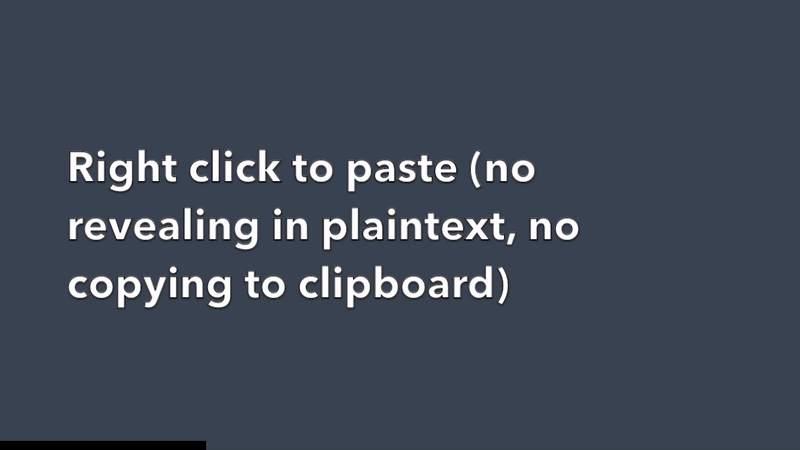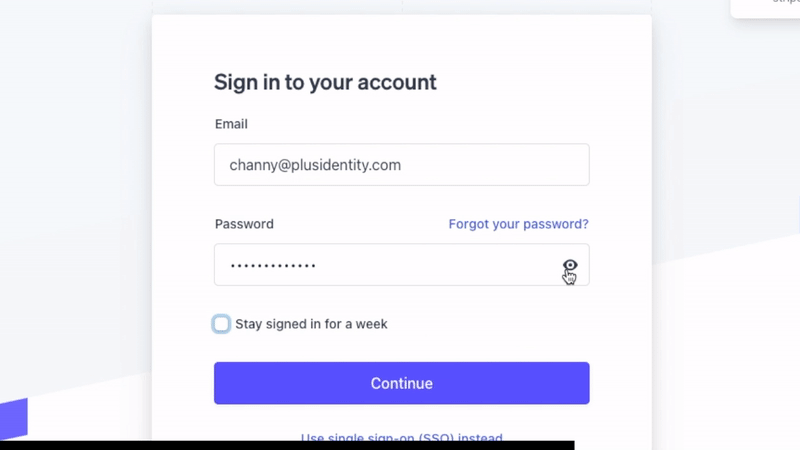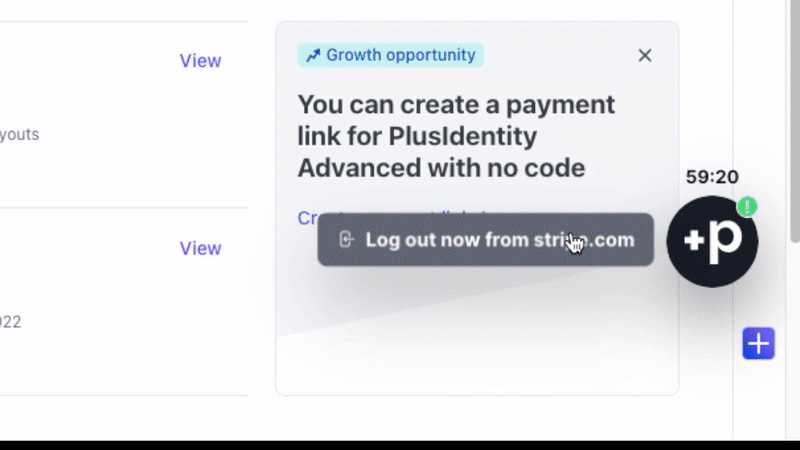
Accessing password.
1. Install browser extension.
2. Decrypt & paste password into password input field via browser extension. (Never revealed in plaintext or copied to clipboard.)
🔐 Why should I trust PlusPassword?
- We take a lot of pride in our robust security design, but the reality is that nothing in this world is 100% failproof.
- That's why we always encrypt your passwords (using industry standard cryptographic practices**) and never store anything on our servers that can ever decrypt them (zero-knowledge).
- Learn more in our security page.
🙏 The Ask
- Try sharing a password through PlusPassword (~30 seconds, free). We also have an awesome Slack app and browser extension (download page, also free).
* With enough malicious intent, one technically can see the plaintext of the password by inspecting the value attribute of the password input field or listening to the POST request when the form is submitted (although most websites only send the hash of the password over the wire). But the thing is, if someone has that much malicious intent to begin with (i.e. going out of their way to dig up the plaintext of the password), you probably shouldn't be sharing the password and giving this person access to your account anyways.
** We never store anything on our servers that can ever decrypt your encrypted passwords (zero-knowledge). We use PBKDF2 (with 101,004 iterations) for key derivation and AES-GCM for symmetric encryption, both utilizing the Web Crypto API. PlusPassword is developed adhering to the compliance requirements of SOC 2 (PlusIdentity is SOC 2 Type II compliant).